Beautiful Tips About How To Detect Cyber Crime

Your enthusiasm about christophe's previous presentation about the computer crime unit convinced us to ask him.
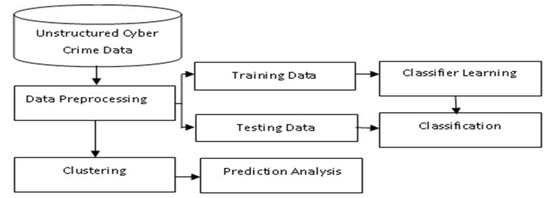
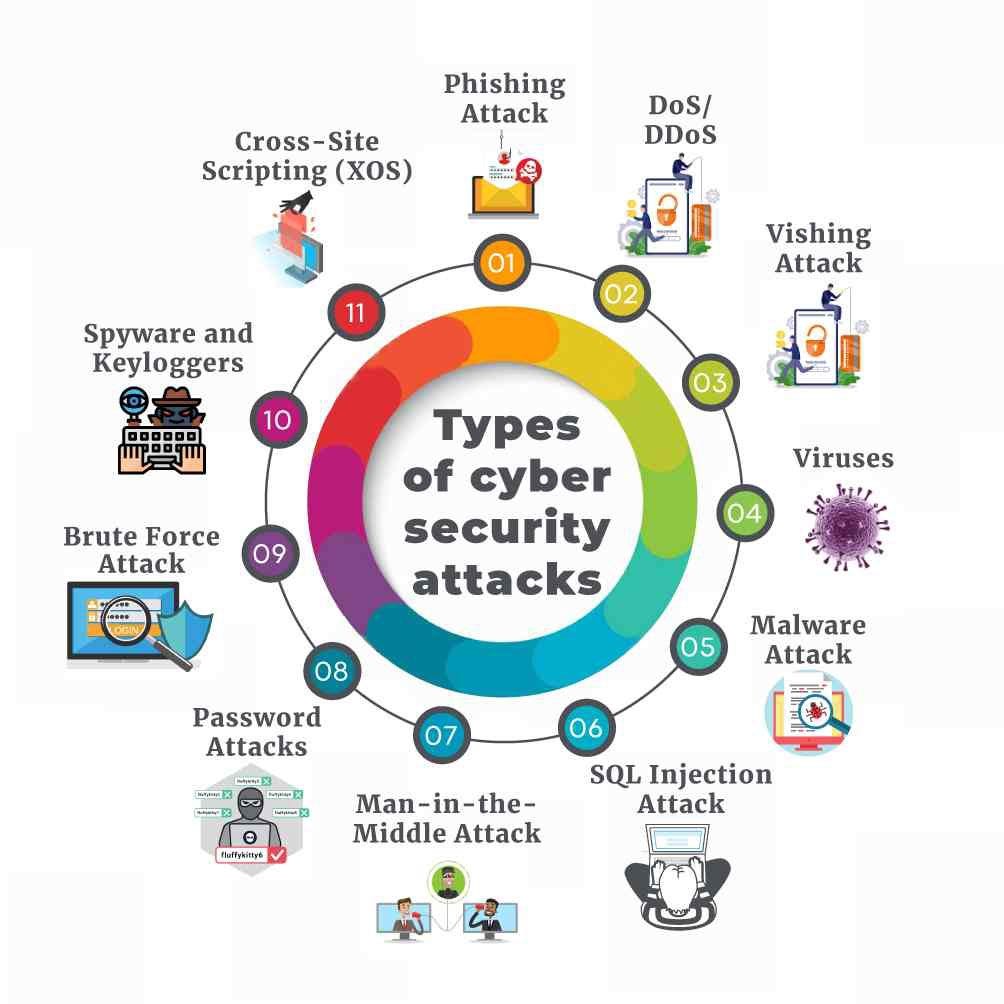
How to detect cyber crime. Not only can collecting security logs help detect cyber criminal activities, but they also become hugely important when dealing with digital forensics to determine root cause analysis and help. Pdf files are often used to spread malicious software or to steal sensitive information. In this dissertation, we design effective techniques for detecting and attributing cyber criminals.
Generally, cyber frauds are similar to each other and have the same scheme of work. Here are 5 key strategies to a successfully detecting and proactively preventing cyber fraud at your organization: Laws, rights and regulations is a unique and important contribution to the literature on cyber.
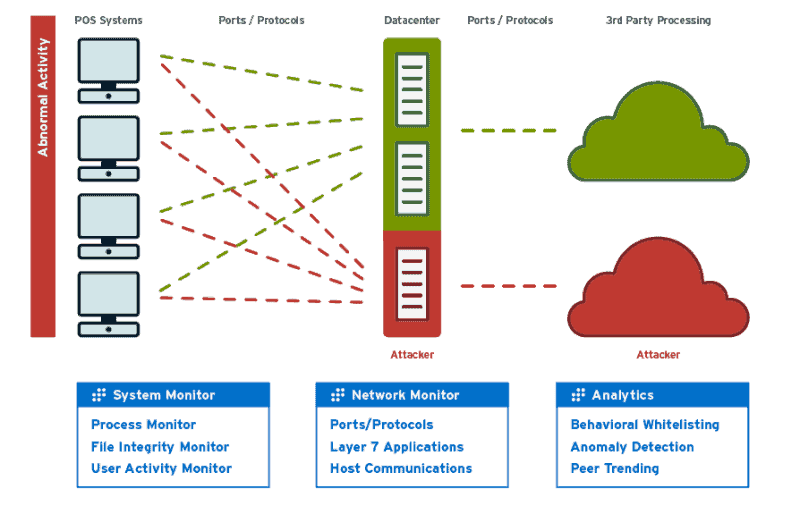
In the simplest terms, malware =. We can do that by detecting attempts to pick the lock. Establish a “gold standard” to detect anomalous and malicious activity on pos systems.
We consider two kinds of fundamental techniques: Almost everyone is familiar with a ‘malware’ after the infamous ‘wannacry’ ransomware attack on networks across the globe. Cyber crime and the victimization of women:
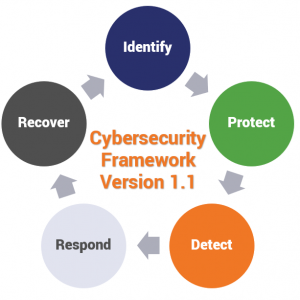
Honeypots are said to be the legitimate parts of the website containing very. How to detect cyber crime? In order to detect cyber crime some techniques are used, which i shall now.
Learn how to use microsoft 365 defender to manage and respond to incidents and alerts in your microsoft 365 tenant. Cyber threats are an ever present and on. How to detect cyber fraud?
Cyber crime is known to change the face of crime for it is more lucrative and harder to detect. Their main characteristic is pressure. Cybercrime is a growing problem around the world.
There are several steps you can.